Provide seamless experiences with account takeover prevention
Protect your customer accounts from account takeover using our login abuse prevention solution. Our login abuse solution detects suspicious activity and stops costly account takeover (ATO) fraud. It can identify card testing fraud as well. Plus, our technology can give your customers a better, seamless experience across your platforms.

How Account Takeover Fraud Prevention Works
We know how valuable customer relationships are — and how important it is to protect them. Our ATO detection technology works quickly and accurately to keep accounts safe.
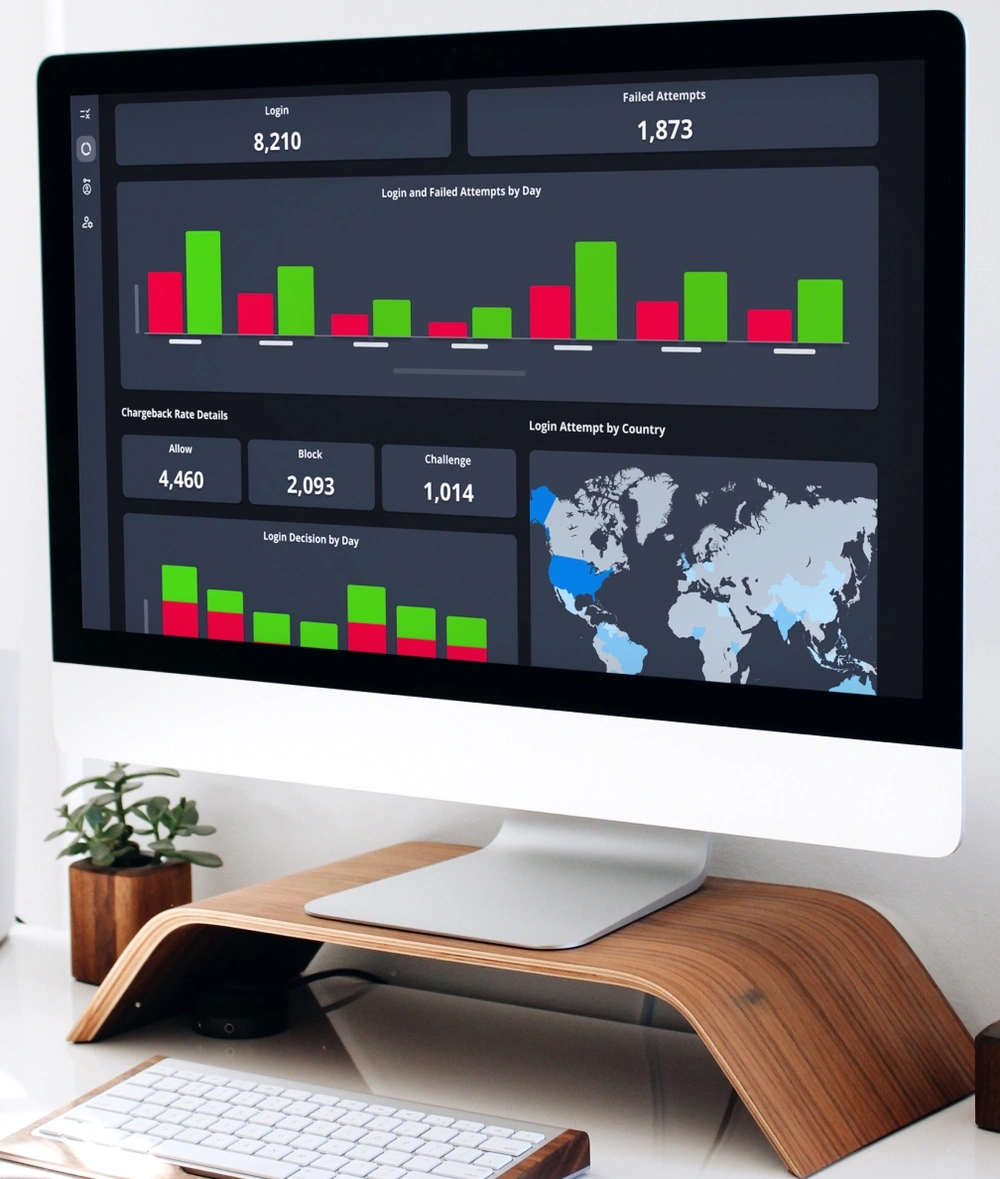
Identity details are collected.
User and device attributes are gathered. Data elements can range from device type and IP address to user location and biometrics.
Login attempt is accepted or challenged.
Within milliseconds, our technology accepts, blocks, or challenges the login attempt. Challenging a login attempt means requiring additional steps to verify a user — such as multi-factor authentication (MFA).
Account activity is monitored.
Once the user gains access to the account, further actions are monitored for suspicious behavior — such as changes made to the delivery address or email.
Your accounts are protected.
You no longer have to worry about harmful events like data breaches and credential stuffing attacks. Our technology has you covered.
Unique features deliver needed benefits
Kount technology provides all the capabilities you need to elevate your account protection strategy.
Identity verification
Determine how risky a customer’s digital identity is during events like account creation and checkout. Spot red flags that could indicate fraud.
Bot detection
Identify the use of bots — a software program that runs automated tasks — to commit fraudulent activities.
Velocity checks
Spot fraud patterns by monitoring the number of times a user tries to interact with your business within a short period of time.
Card testing detection
Detect card testing on zero dollar authorization attempts or payment events.
Benefits you can’t afford to miss
Customer loyalty and confidence is what helps your brand flourish. Show your customers how much they mean to you with account takeover fraud protection — and reap the benefits to your business.
Protect sensitive account information
Customers store payment information, loyalty points, and sensitive data on their accounts. Maintain their trust by keeping fraudsters out of user accounts.
Enhance customer experiences
Set up policies to eliminate friction for known customers trying to log in or make purchases on your platforms. Give your customers an easy, seamless experience.
Maintain positive brand reputation
Preventing ATO fraud keeps your brand image healthy. You don’t have to worry about negative online reviews or news stories that can damage your reputation.
Eliminate ATO attacks
Don’t waste time and money on recovering from an ATO attack. Keep your valuable resources focused on innovating and growing your business.
Improve data analysis
Enrich your own data with login trend data — including device and IP information — that is often not available to fraud teams. Evaluate the data in real time to update policies and keep pace with evolving threats.
Reduce payments fraud
Account protection is the first step towards payment fraud prevention — stopping fraudsters at the door. Block access to stored debit or credit cards, stop unauthorized transactions, and avoid chargebacks.
Added value achieves better results
Account protection just makes sense. But why choose Kount? Here’s what sets us apart from any other strategy.
Global data network
Kount has decades worth of data — and the most robust data network you can find. As part of the Equifax family, Kount has access to global insights from both digital and physical interactions. And the better your data, the better your decisions will be.
Simplified authentication
Our technology analyzes billions of data elements to identify risky account activity and suspicious login attempts. And Kount is the one of the first platforms to offer a frictionless — yet completely accurate — authorization process. Less friction means better experiences for your customers.
Advanced AI and machine learning
Kount is the only service provider on the market today to use two forms of machine learning — supervised and unsupervised. More advanced technology produces better results. Plus, the quality of data that feeds our machine learning is unmatched. Thus, giving you reliable and accurate decisions.
What our clients are saying
QUESTIONS & ANSWERS
Frequently asked questions about account takeover fraud prevention.
Account takeover (ATO) fraud is a type of cyber attack. During an attack, a fraudster gains unauthorized access to online accounts — such as social media, bank, and email accounts. After gaining access to accounts, the fraudster will steal payment information, withdraw money, change account credentials, or make fraudulent purchases.
ATO fraud can be devastating to your business. Financially speaking, a single account takeover attack can cost hundreds of thousands of dollars or more. On top of that, you may need to repair security systems, refund affected customers, and save your brand reputation. The recovery process can be incredibly draining on you and your staff.
It’s difficult to imagine that this kind of fraud could ever happen to you. But it’s extremely common in today’s digital commerce world. At the end of the day, it’s better to have protection in place before an attack happens.
Typically, account takeover fraud attacks occur because of a data breach, poor account security, social engineering, and phishing scams. We’ll break that down a little further.
Data breach
A data breach is a security violation. Typically, cybercriminals find weaknesses in a company’s security systems that give them access to sensitive information — such as consumer data, passwords, email addresses, and payment card numbers. Cybercriminals then sell the information on the dark web to fraudsters that use it to carry out ATO attacks.
Poor account security
Customers often reuse the same easy-to-guess password across multiple online accounts. On top of that, some businesses don’t have controls in place to block suspicious login attempts. The result is poor account security. And fraudsters can easily take advantage of this weakness by testing hundreds of username and password combinations until they find a list of matches.
Social engineering
Social engineering is a form of manipulation and deception used to get personal or sensitive information. Fraudsters use a variety of tactics to get account credentials or access to sensitive company information.
For example, a fraudster may call a customer service department and pretend to be a distressed customer who is having trouble getting into an online account. The fraudster may act extremely emotional or angry to get the customer service agent to give away account information.
Phishing scams
Phishing scams are attempts to trick someone into sharing personal information or installing malware on a device. Typically, a fraudster will send an email from a made-up company that looks legitimate. The email may include an intimidating message and a link to a website where recipients will input their login credentials or download malware.
For example, let’s say a fraudster sends an email to victims that appears to be from a water utility company. The email tells recipients that they have past due charges and their water will be shut off if they don’t pay the bill. Included is a link to pay the bill. However, when recipients follow the link, they are directed to a fake website. And when they input their credentials, the fraudster steals them.
Corporate account takeover (CATO) is a cyber attack where fraudsters try to gain access to corporate bank accounts. Once they breach the account, they can send money to their own accounts through the ACH.
CATO attacks are very similar to regular account takeover threats. The only difference is that fraudsters typically have access to a larger amount of money when they break into corporate accounts. So the damage done to your business can be more devastating and long-lasting.
To detect ATO attacks, you first need to have monitoring tools that can provide insight into your web traffic. Once you have tools in place, there are a few warning signs to watch for.
1. Increased web traffic.
If you see a sudden spike in web traffic outside of peak times (during holidays or major marketing events), it could be a sign that fraudsters are trying to hack into accounts via a credential stuffing or brute-force attack.
2. Unusual account activity.
It’s common for customers to forget their passwords or change their account information from time to time. What isn’t common are excessive failed login attempts, multiple password reset requests, and changes to the back-up device or email address where one-time passwords are sent. If you notice an influx of this kind of activity, a fraudster could be trying to hack into customer accounts.
3. Increased customer support requests.
Another warning sign of ATO fraud is a sudden uptick in customer support calls or help tickets — particularly around account access or activity. Fraudsters may attempt to manipulate customer service agents into giving up account information by pretending to be a distressed customer.
There are a number of actions you can take to prevent account takeover attacks. Adding these extra security policies and practices to your business can help you prevent other types of fraud from happening.
1. Implement multi-factor authentication (MFA).
Multi-factor authentication is a verification process that requires users to provide two or more forms of identification. For example, users may have to enter a password and a code sent to their email or answer a secret question to get into an account.
The best time to require MFA would be after multiple failed login attempts or requests to change account credentials. Typically, fraudsters won’t have access to the phone or email tied to an account, so MFA protocols could prevent them from getting in.
2. Improve your business’s password policies.
Weak passwords give fraudsters a better chance of success. Implement strong password requirements for customers when they sign up for an account with you. And make sure your employees follow those same guidelines for any accounts that are connected to your business.
3. Add account lockout policies.
If you really want to be safe, set up policies that block further logins after two or three failed attempts. Sometimes customers can misspell or forget their passwords, so you could potentially lock out a legitimate customer. However, it’s better to overprotect accounts, especially if they are tied to payment cards, banking information, digital wallets, or any other financial asset.
4. Educate employees.
Social engineering and phishing tactics are always evolving — becoming more sophisticated as technology advances. Make sure your employees are aware of popular scams and understand the signs of social engineering so they don’t make the mistake of giving fraudsters unauthorized access to accounts or sensitive information.
5. Use technology.
There are a variety of tools out there that can help you mitigate account takeover attacks. Fighting fraud is incredibly time-consuming, costly, and prone to errors, so doing it all on your own can be stressful and challenging. Thankfully, there are experts out there that can help. Fraud prevention software like Kount not only stops fraud attacks, but also reduces friction for good customers. So you can block the bad without hurting the good.
Talk to an Expert
GET STARTED TODAY
Prevent account takeover and enhance customer experiences
Thousands of companies from all over the world use Kount’s trust and safety technology to protect their user accounts. Will you be next? Sign up for a demo today, and see what it’s like to have confidence in every interaction.